A zero-day vulnerability * affects all currently supported versions of Microsoft’s operating system: Windows 10, the recent release 11, and Windows Server. The flaw, confirmed by the Bleeping Computer researchers, makes it possible to obtain the elevation of privileges and concerns Windows Installer. Compounding the story is the fact that it is already in circulation malware that exploits the exploit.
There is no point in updating the machine with the latest security patches because Microsoft has not been able to fix the vulnerability so far. He emphasizes it Abdelhamid Naceri, a researcher who first demonstrated the possibility of exploiting the exploit, despite the flaw having been reported to the company and Microsoft had tried to correct it with the updates included in this month’s Tuesday patch. This variant was discovered during the analysis of the CVE-2021-41379 patch, the bug was not fixed, underlines Naceri.
The researcher unveiled the details of the new variant and Bleeping Computer was able to show how it works, documenting it with a video. Through the exploit, it is possible to open a command prompt with SYSTEM privileges starting from an account with standard privileges.
The story is also causing discussion for another reason: Naceri has publicly revealed the variant of the exploit without first informing Microsoft. This unorthodox behavior was motivated by Naceri as a form of protest for the progressive reduction of rewards under the Microsoft Bug Bounty program (provides rewards for developers who identify more or less serious vulnerabilities related to Microsoft products).
Microsoft intervened on the case, noting that it will develop the appropriate corrections
We are aware of the disclosure and will do what is necessary to protect our customers. An attacker using the methods described must already have access and the ability to execute code on the victim’s computer.
Naceri himself invites you to wait for the release of a new patch because the complexity of the vulnerability makes it difficult to create third-party corrective measures: any attempt to fix the binary directly will damage the Windows Installer. So better wait and see how Microsoft develops the new patch.
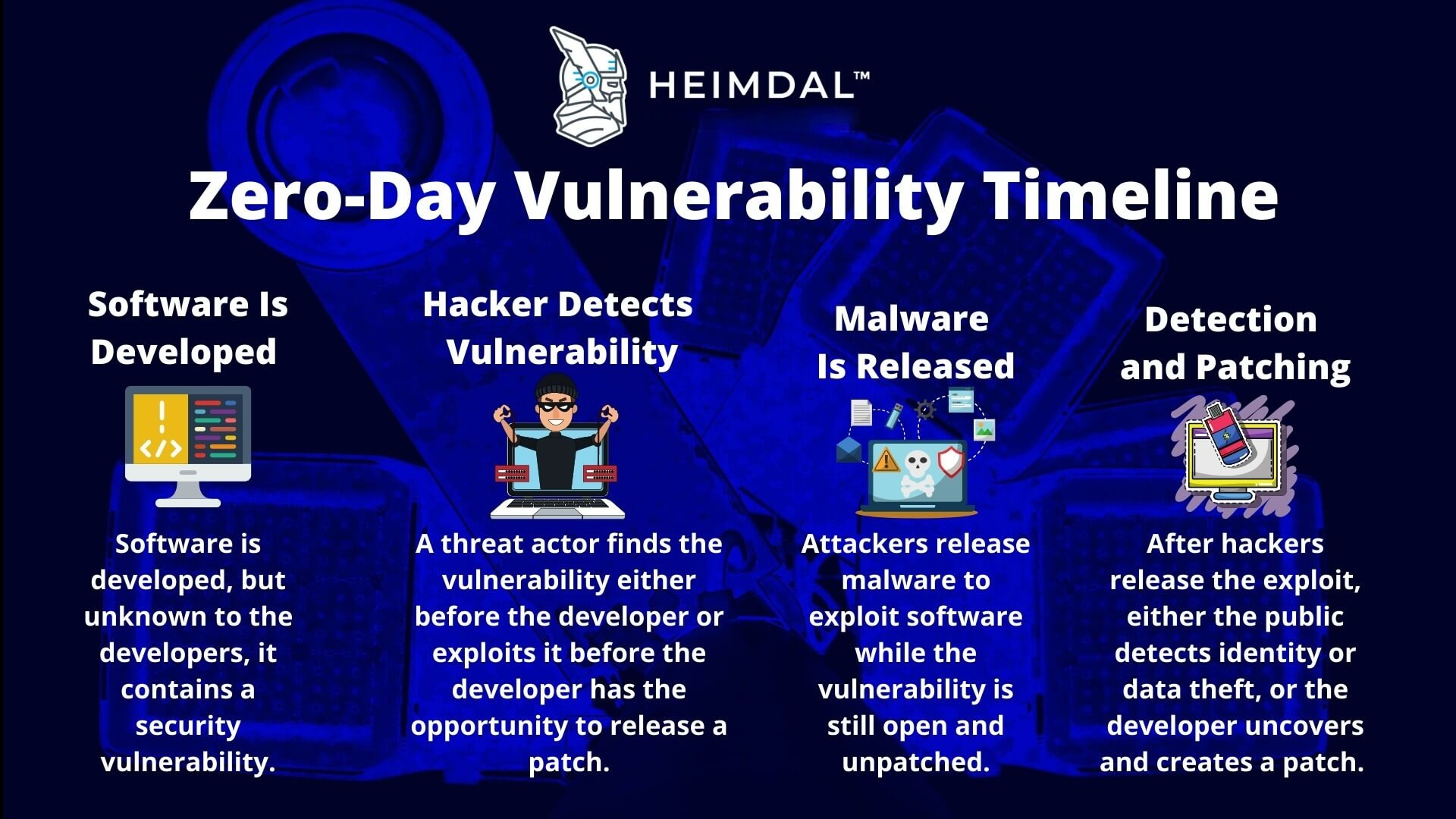
* Zero-day indicates a vulnerability discovered by attackers or security researchers before software vendors. Precisely because the software vendors are unaware of it, there are no ready-made patches for zero-day vulnerabilities. The zero-day exploit is the method used to exploit a zero-day vulnerability.
Note: Article adjusted to clarify the meaning of the term zero-day